Botnets are networks of computer devices that have been hijacked and used to carry out scams and cyber-attacks. The term “botnet” is a combination of the words “robot” and “network”.
How It Works: Basic Construction Steps
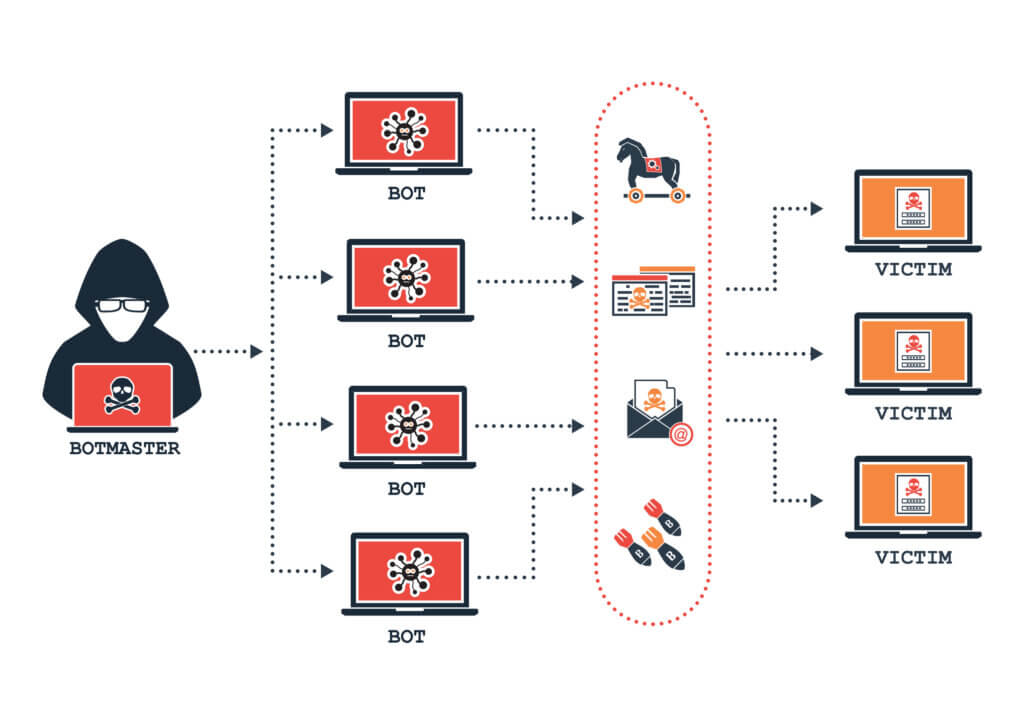
Prepare and Expose:Hackers exploit vulnerabilities to expose users to malware. The aim is to prepare the user to be infected without their knowledge.
Infect:Users’ devices are infected with malware. Methods include social engineering and drive-by downloads.
Activate:The attacker takes control of the infected devices. The zombie computers are organized into a network of “bots”.
Botnet functionalities:
- A zombie computer allows administrative-level operations such as:
- Read and write system data. Collect the user’s personal data. Sending files and monitoring activities. Search for vulnerabilities in other devices. Install and run applications.
Objectives of Botnet Creators
- Financial theft (extortion or outright robbery).
- Information theft (access to sensitive accounts).
- Sabotage of services (taking down websites, etc.).
How to identify if you are a victim of this practice
Your computer’s CPU is working at high power;
- When you use a USB stick, the system tells you that it is infected;
- Shortcuts or files are created on removable drives (pendrives);
- Some folders are hidden on the computer;
- You can’t access the Windows settings, which are locked;
- Network traffic is high;
- You send emails, but you don’t receive them;
- Your mobile bill payments are not made;
- The device’s battery runs out faster than usual and often remains warm;
- Unknown users or administrators appear among the computer’s services.
What to do to avoid
- Antivirus and antispyware programs:
- Installing a good antivirus and antispyware program is essential. They help detect and remove known threats. Remember to keep them up to date so that they are always prepared to face the new tricks of cybercriminals.
- Software updates:
- Keeping all your programs up to date is like giving your computer a suit of armor. Frequent updates correct vulnerabilities and close doors to possible intrusions. Set up automatic updates whenever possible.
- Strong Passwords:
- Passwords are like the keys to your digital castle. Use complex passwords, combining uppercase and lowercase letters, numbers and special characters. Avoid using obvious personal information and never share your passwords.
- Firewall Enabled:
- The firewall is like the guard on the drawbridge. It monitors incoming and outgoing traffic, blocking suspicious activity. Never disable the firewall, even for a brief moment.
- Be careful with flash drives:
- Flash drives are like messengers that can bring poisoned gifts. When connecting a USB stick, check that it is not infected. Avoid using USB sticks of dubious or unknown origin.
